Apple has been granted a patent (number US 11777936 B2) for “Friend Key Sharing.” It involves sharing access to a house and presumably a car via an electronic“friend key.”
About the patent
The patent relates generally to controlling access to electronically-secured property, and, more specifically, to securely permitting access by an owner to another individual. In the patent Apple notes that traditional techniques for gaining access to functionality of a system (e.g., physical access or accessing some function of the system) include use of physical keys or electronic key fobs.
Carrying such traditional keys may be inconvenient and may allow malicious entities to gain access if a key is lost or stolen. In other cases, a password, secret code (e.g. personal identification number (PIN)), or other secret known to the owner can be used to permit access. What’s more, in modern systems, biometric data identifying the owner is used. Combinations of these techniques can also be used.
In some cases, the owner of the system wishes to permit another individual to access the system. If access is controlled by a physical key or fob, the owner must physically deliver the key/fob to the individual and then must physically retrieve the key/fob after the individual is finished with access. If access is controlled by secret data, the owner must communicate the secret data to the individual.
If the communication is insecure, a third party can observe the secret data. Additionally, the secret data must be changed after the individual is finished with access to re-secure the system with respect to the user. If the system is secured by biometric data, the system generally can’t be accessed by the individual without the owner being present. Each of these options can limit the feasibility of permitting access.
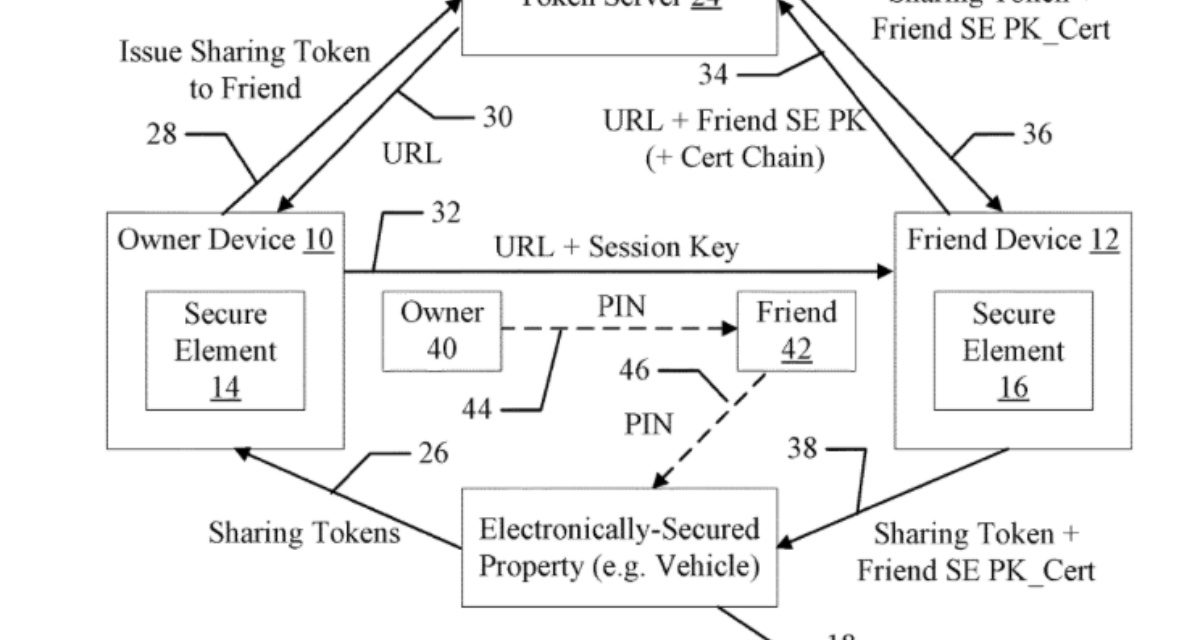
Apple’s solution is an electronic “friend key.” That is, a token that could be stored and shared, for example, via an iPhone or Apple Watch.
Summary of the patent
Here’s Apple’s abstract of the patent: “Techniques are disclosed relating to sharing access to electronically-secured property. In some embodiments, a first computing device having a first secure element receives, from a second computing device associated with an owner of the electronically-secured property, an indication that the second computing device has transmitted a token to server computing system, the token permitting a user of the first computing device access to the electronically-secured property.
“Based on the received indication, the first computing device sends a request for the transmitted token to the server computing system and, in response to receiving the requested token, securely stores the received token in the first secure element of the first computing device. The first computing device subsequently transmits the stored token from the first secure element of the first device to the electronically-secured property to obtain access to the electronically-secured property based on the token.”
Article provided with permission from AppleWorld.Today