MDM Technologies
Contents
MDM technologies
Before exploring how you can use MDM for device management, let’s look at the technologies that enable MDM on iOS. MDM capabilities are built on existing iOS technologies such as managed configuration profiles, over-the-air enrollment, and the Apple Push Notification Service (APNS). You can leverage these technologies by using third-party MDM solutions.
Managed profiles
Managed profiles are configuration profiles installed on devices by the MDM server. This managed profile is analogous to GPO and MCX for the desktop and laptop management in an organization. These managed profiels can be locked to prevent end users from removing them. Once the managed profile has been delivered via enrollment, the profile is completely managed by the MDM server.
There’s no limit to the number of managed or unmanaged configuration profiles that you can install on a device.
The MDM server is designed to update and removes managed profiles, at the complete control of the IT administrator. Because the primary MDM profile must be unlocked, end users can opt out and delete this profile at any time. The end user always has these options available:
- Opt out of MDM altogether – iOS removes all managed profiles and associated data. The trust relationship with the MDM server is revoked and further push notifications from the MDM server will yield no results.
- Remain under management – the user has complete control to remove one or more of the profiles on their device, yet still allow some (or all) level of management by the MDM.
Over-the-air enrollment
iOS over-the-air (OTA) enrollment and configuration allows you to configure mobile devices securely, without a physical connection to a host computer running iPCU. MDM uses Simple Certificate Enrollment Protocol (SCEP) to leverage the OTA framework for enrollment.
The protocol is designed to make the issuing and revocation of digital certificates as scalable as possible. The idea is that any standard network user should be able to request their digital certificate electronically and as simply as possible.
The process of OTA enrollment involves three parts:
- Authentication – The end users authenticate into the MDM server. This process builds our chain of trust, ensuring that the requests are coming from authenticated users within our network. User authentication can be enforced at the time the end user visits the enrollment URL. OTA authentication can use any web authentication scheme, on any published mechanism
- Certificate enrollment – After the end user is authenticated, the device uses the SCEP to generate a certificate enrollment request. This request communicates directly with the enterprise CA and enables the device to receive an identity certificate from the CA in response.
- Device configuration – The third phase of OTA enrollment is profile delivery and configuration. This is a process that is repeated each time a new configuration profile is sent to the device or group of devices. In this part of the process, the MDM server sends an encrypted configuration profile that’s been built for a specific or group of devices. The user must agree to install this profile, authenticating to the device as necessary, then the MDM server takes over and has control to make changes, as necessary.
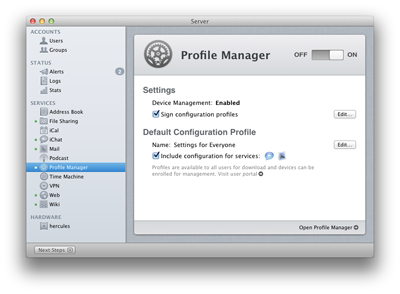
Figure 12 – Apple’s Profile Manager
Mobile Device Management Solutions
Users have a wide range of choices for MDM providers, each having strengths and weaknesses. It is important to ask the right questions and assess which of the solutions will fit your organization the best. Apple maintains a list of iOS-friendly MDM providers and also offers their own solution, built right into Lion Server.
For a list of iOS MDM providers, visit http://www.apple.com/iphone/business/integration/mdm/. For more information on Apple’s MDM solution, visit http://www.apple.com/macosx/server/.
