Configuration Profiles
Contents
Configuration Profiles
Configuration profiles are lists of settings that IT departments use to quickly set up iOS devices. These profiles may be setup to configure end users’ devices to access Microsoft Exchange servers, the corporate VPN tunnel, Wi-Fi networks and corporate resources. Configuration profiles also give IT the ability to lock the settings.
Configuration profiles can be created with the iPhone Configuration Utility (iPCU), a free application for Mac OS X (10.6.x and 10.7.x) and Windows (XP, Vista and 7).
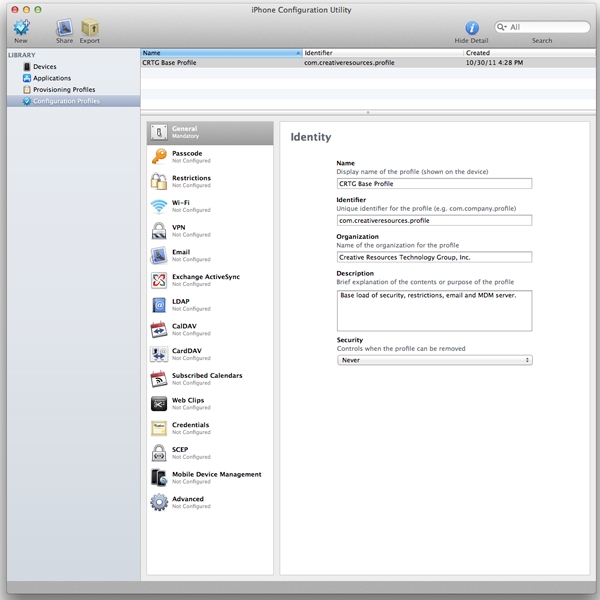
Figure 4 – iPCU Configuration Profiles
What are configuration profiles?
A configuration profile is an XML file that can be used to distribute configuration information to iOS devices. IT administrators will use these configuration profiles to configure specific, single or multiple, settings for iOS devices. Each configuration profile contains one or more “payloads,” which detail out all of the settings that one can possibly set on an iOS device, which include:
- Passcode – requirement of passcode, simple vs. complex passcode
- Restrictions – locking down Safari, YouTube, iTunes, installation of apps, deletion of apps, allowed content
- Wi-Fi – networks SSID’s and passwords (any standard 802.11x wireless network)
- VPN – Cisco IPSec, L2TP, PPTP, SSL VPN
- Email – Standards-based email, contacts, and calendars (IMAP, POP, CardDAV and CalDAV)
- Exchange ActiveSync – supporting Exchange Server 2003, 2007 and 2010
- LDAP – directory service settings
- CalDAV – calendar service settings for shared calendars
- CardDAV – group address book
- Subscribed Calendars – read only access to shared calendars
- Web clips – URL’s to a specific website, shortcut
- Credentials – PKCS1 and PKCS12 certificates to install on the device
- SCEP – Simple Certificate Enrollment Protocol allows the device to obtain certificates from a certificate authority
- Mobile Device Management – configures the device so that its configuration is managed over the air by an MDM server
- Advanced – Cellular network settings (APN)
Best Practices for Protecting Configuration Profiles
Administrators should sign and/or encrypt a configuration profile to prevent it from being altered or viewed. You can also protect a configuration profile by locking it with a passcode so that an end user can’t remove it.
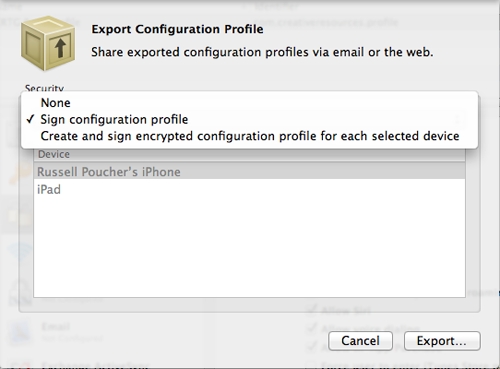
Figure 5 – Setting Security
Signing and encryption
The data on a configuration profile can contain sensitive information such as account information and passwords. iPCU allows three options for exporting out the profiles you have built and protect your data.
A signed profile may only be replaced by another profile with the same Identifier and signed by the same copy of iPCU. iPCU may be used to both encrypt and sign configuration profiles, locking them down to a specific device and preventing others from changing or viewing the settings of the profile.
Security on profiles is available as follows, upon Export:
- None – Creates a plain text .mobileconfig file that can be installed on any device. Data is not encrypted and may be viewed in any text editor. There is no security in place.
- Sign configuration profile (good security) – Creates a signed .mobileconfig file that can be installed on any device, provided the profile hasn’t been altered. After installation, the profile can be updated only by another profile with the same Identifier and signed by the same copy of iPCU. The profile is signed with the public key associated with a device’s identity certificate. This public key can be obtained by connection through USB to a computer running iPCU or using over-the-air enrollment.
- Create and sign encrypted configuration profile for each selected device (best security) – Signs the profile so it cannot be altered, encrypts all the contents so the profile cannot be viewed in a text editor, and can be installed only on specific devices that appear in the Devices list. Separate .mobileconfig files are created for each of the devices you select from the Devices list. In most cases, this is the best option to select and offers the highest amount of security.
Locking Profiles
A profile may also be distributed that’s locked to a device so that after it’s installed, it can be removed only by wiping the device of all data (full reset) or, by entering a passcode. Locking a configuration profile is recommended to prevent end users from deleting it from a device. The following three choices are available for locking:
- Always – The end user may remove the profile at any time.
- With Authorization – Password is set, and needed, for removal of profile.
- Never – Profile may only be updated with a new version, but not be removed.
Installing configuration profiles
Profiles can be installed via one of several methods:
Figure 6 – Hard-wired USB Connections
- USB – for smaller installations, this is a viable way of getting payloads onto your mobile devices. As the quantity goes up, the benefits to this method go down and it becomes much more work. This process is, typically, done by IT directly. The USB method is meant for low-quantity deployments, such as 50 or less devices.

Figure 7 – Wireless Connections - Wirelessly – Profiles can be distributed wirelessly via email, website and over the air. When an end user downloads the profile from the web or opens it as an attachment in Mail, the device recognizes the .mobileconfig extension as a profile and begins installation when the user taps Install. If a passcode has been set on the device, the user will be prompted to enter in their credentials.
- Email – Distribution of profiles via email. The end user receives the email message on the iOS device and then taps on the attachment to install the profile. This process does require the end user to accept and install.
- Website – Distribution of profiles via a corporate website require the user to follow a specific link to download a profile. The end users can navigate to the web page on their device and then download the profile onto it. This process does require the end user to accept and install.
- Over the air – IT can use a secure enrollment and configuration process enabled by the Simple Certificate Enrollment Protocol (SCEP) to distribute encrypted configuration profiles over the air. SCEP does require some infrastructure to be setup, but makes the process much easier for IT departments to manage in the long run.
