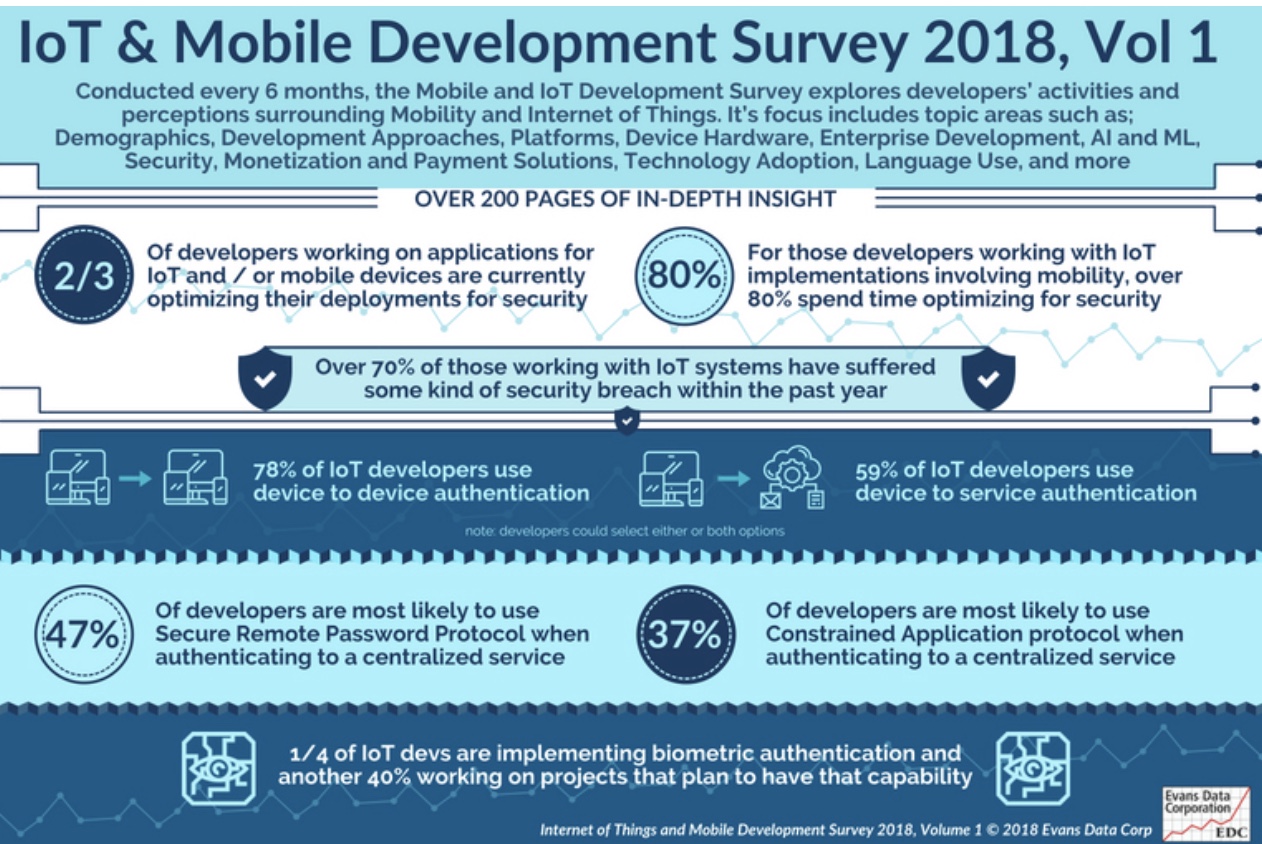
More than two thirds of developers working on applications for IoT and/or mobile devices are currently optimizing their deployments for security according to Evans Data’s newly released IoT and Mobile Development Survey. This is especially true for those working with IoT implementations that also involve mobility where over 80% spend time optimizing for security.
The July 2018 survey also showed that over 70% of those working with IoT systems have suffered some kind of security breach within the past year, thus compelling them to scrutinize their security systems.
Authentication is a critical component of any security system and 78% of IoT developers report they currently use device to device authentication while 59% use device to service (note; developers could select either or both options). For authenticating or authorizing connectivity to a centralized service (cloud, edge etc) developers are most likely to use Secure Remote Password Protocol (47%) followed by Constrained Application protocol (37%).
“While it’s clear that IoT has a very compelling need for security optimizations,” said Janel Garvin, CEO of Evans Data, “there are also new advances that help developers secure their connected device projects. For example, we found that biometric authentication has come a long way recently with now over a quarter of IoT developers implementing some biometric authentication and another 40% working on projects that are planned to have that capability.”
Conducted every six months, the Mobile and IoT Development Survey explores developers’ activities and perceptions surrounding Mobility and Internet of Things. It’s focus includes topic areas such as; Demographics, Development Approaches, Platforms, Device Hardware, Enterprise Development, AI and ML, Security, Monetization and Payment Solutions, Technology Adoption, Language Use, and more.