Upcoming iPhones and iPads could recognize individual users and adjust accordingly, per a new patent (number 20100207721) for systems and methods for identifying unauthorized users of an electronic device at the US Patent & Trademark Office.
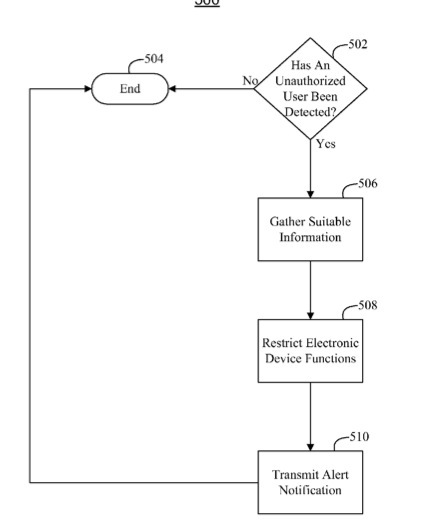
The patent is generally directed to identifying unauthorized users of an electronic device. In some embodiments, an unauthorized user of the electronic device can be detected by identifying particular activities that may indicate suspicious behavior. In some embodiments, an unauthorized user can be detected by comparing the identity of the current user to the identity of the owner of the electronic device. When an unauthorized user is detected, various safety measures can be taken.
For example, information related to the identity of the unauthorized user, the unauthorized user’s operation of the electronic device, or the current location of the electronic device can be gathered. As another example, functions of the electronic device can be restricted. In some embodiments, the owner of the electronic device can be notified of the unauthorized user by sending an alert notification through any suitable medium, such as, for example, a voice mail, e-mail, or text message. The inventors are Taido Nakajima, Pareet Rahul and Gloria Lin.
Here’s Apple’s background and summary of the invention: “People often possess and carry around a variety of electronic devices, such as, for example, cellular phones, PDA’s, personal e-mail or messaging devices (e.g., a Blackberry), and handheld media players (e.g., an iPod). Many of these electronic devices are used frequently by their owners, and the electronic devices may contain personal or sensitive information stored within them. For example, the electronic devices may contain information such as credit card numbers, passwords, social security numbers, bank information, contact lists, or calendar information. Accordingly, if the electronic device is lost or stolen, the loss of the electronic device can be exceedingly disruptive to the owner’s peace of mind and security. Thus, the owner may desire to find out where the lost electronic device is located or who may have gained possession of or stolen the electronic device.
“Systems and methods for identifying unauthorized users of an electronic device are provided. In particular, systems and methods for detecting an unauthorized user, gathering information related to the electronic device, the unauthorized user, or both, and transmitting an alert notification to a responsible party for the electronic device are provided.
“In some embodiments, an unauthorized user can be detected by comparing the identity of the current user to the identities of authorized users of the electronic device. For example, a photograph of the current user can be taken, a recording of the current user’s voice can be recorded, the heartbeat of the current user can be recorded, or any combination of the above. The photograph, recording, or heartbeat can be compared, respectively, to a photograph, recording, or heartbeat of authorized users of the electronic device to determine whether they match. If they do not match, the current user can be detected as an unauthorized user.
“In some embodiments, an unauthorized user can be detected by noting particular activities that can indicate suspicious behavior. For example, activities such as entering an incorrect password a predetermined number of times in a row, hacking of the electronic device, jailbreaking of the electronic device, unlocking of the electronic device, removing a SIM card from the electronic device, or moving a predetermined distance away from a synced device can be used to detect an unauthorized user.
“In some embodiments, when an unauthorized user is detected, information related to the current user of the electronic device (e.g., the unauthorized user), the current user’s operation of the electronic device, the electronic device’s location, or any combination of the above can be gathered. For example, information such as the current’s user’s photograph, a voice recording of the current user, screenshots of the electronic device, keylogs of electronic device, communication packets (e.g., Internet packets) served to the electronic device, location coordinates of the electronic device, or geotagged photos of the surrounding area can be gathered.
“Instead or in addition, when an unauthorized user is detected, various functions of the electronic device can be restricted. For example, access to particular applications can be restricted, access to sensitive information can be restricted, sensitive information can be erased from the electronic device, or any combination of the above.
“In some embodiments, an alert notification can be sent to a responsible party when an unauthorized user is detected. The ‘responsible party’ can be any persons suitable to receive the alert notification, such as, for example, the owner of the electronic device, proper authorities or police, persons listed in a contact book in the electronic device, or any combination of the above. In some embodiments, the alert notification can be a general warning that an unauthorized user has been detected (e.g., ‘Warning, your electronic device may have been stolen’). In some embodiments, the alert notification can contain any of the information gathered in response to an unauthorized user being detected (e.g., photographs, voice recordings, screenshots, geotagged photographs, or any other gathered information).
“The alert notification can be transmitted to the responsible party through any suitable medium. For example, the alert notification can be sent as a voicemail, phone call, text message, e-mail, or facsimile. As another example, the alert notification can be sent through any suitable VoIP application (e.g., Skype or Windows Live Messenger), instant messaging application (e.g., AOL Instant Messenger or MSN Messenger), on-line profile application (e.g., Facebook or Friendster), blog application (e.g., Twitter or Xanga), or ‘cloud’ server (e.g., sent to a Mobile Me account associated with the owner of the electronic device).”