Intel's abstract
A method, apparatus and system for improving usability of virtual machines is described. A console module on a VM host may continuously monitor incoming data (e.g., files and/or attachments) and make automatic determinations regarding how and/or whether to intercept, route, redirect and/or deliver the data (e.g., where to store files, when and/or whether to deliver the files, execute the files, etc.). Additionally, in one embodiment, a unification console may be provided to enhance the usability of the VM host. The unification console enables the user to view the VM host via a unified desktop interface while handling the underlying switching and/or interactions between VMs.
Patent excerpts
According to one embodiment of the present invention, a console module on a VM host may continuously monitor and/or filter incoming and/or outgoing data (e.g., file requests, network ports/streams (e.g. Hyper Text Transport Protocol ("HTTP")), files, streams and/or attachments) and make automatic determinations regarding how to manage the data (e.g., where to store files, when and/or whether to deliver the files, execute the files, etc.). In one embodiment, the console module may perform such monitoring and/or filtering at "choke points" in and out of the VMs running on the VM host, i.e., points on the VM through which all input/output (I/O) to and from the VM typically traverse.
In addition to the overwhelming task of managing the VM partitions, users also have to handle the proliferation of viruses and other such computer "attacks", which are becoming increasingly more common. A typical mode of attack for a computer virus, for example, is to send an electronic mail message (email) containing a file attachment to an unsuspecting user's computer. The file attachment may contain malicious attack data, and the email may contain some inducement for the user to launch the file attachment. When the user clicks on the file attachment, the attack data embedded in the file may be executed. The attack data may then access an address book and send the file attachment in an email to addresses found in the address book. The attack data may then try to modify files on the user's computer or obtain other files and mail them back to the attackers. It is well known in the art that various other modes of attack may also be employed other than email.
Embodiments of the present invention provide users with an improved management scheme that enhances the usability of virtual machines. More specifically, embodiments of the present invention improve usability and security in a virtualized environment. It improves usability, for example, by simplifying management of the VM partitions and automating the classification, replication, filtering and/or transforming of data and/or data requests entering and leaving these partitions.
Embodiments of the present invention provide for improved VM management, e.g., by simplifying file management within the VMs and ensuring that VMs on the host are isolated from potentially harmful and/or malicious data. Thus, in one embodiment, a module on Host 100 may automatically perform all of the content management on the host, e.g., handle all incoming data received by the host and making decisions such as where to deliver and/or store the data, deciding when and/or where to execute the data and/or whether to provide one or more of the VMs on the host with access to the data. By automatically making these determinations based on predetermined criteria, this scheme effectively enhances the user experience (because the user does not have to understand the underlying structure/organization of the VMs on the host) as well as provides a mechanism to decrease the likelihood of malicious data infecting multiple VMs (e.g., by enforcing a security policy such as isolating suspicious data into a predetermined VM).
Handling an email with an attachment
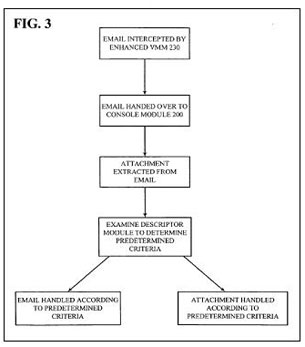
Patent FIG. 3 is a flowchart that conceptually illustrates an example of how descriptors may be utilized to automatically handle an email with an attachment. As previously described, although the example focuses exclusively on email, embodiments of the invention are not so limited and may include any and/or all data accessed by and/or received by Host 100. Additionally, although the following operations may be described as a sequential process, many of the operations may in fact be performed in parallel and/or concurrently. In addition, the order of the operations may be re-arranged without departing from the spirit of embodiments of the invention.
In the example illustrated conceptually in the flowchart of FIG. 3, an incoming email may be intercepted by Console Module 200. The email attachment may be extracted from the email and based on various predetermined criteria, Console Module 200 may determine how to handle the attachment. For example, Console Module 200 may determine where to send an incoming attachment based on the attachment type (e.g., a Word file, a JPEG, an MPEG video file, etc), and not based on the original destination for the communication. Thus, if the incoming attachment is a video file and Descriptors 250 indicates that (a copy of) all video files are to be stored in VM 120, Console Module 200 may extract and store the attachment in VM 120. This extraction and storage may be invisible to the user, who may merely know that he/she has received an email with an attachment.
When the user attempts to launch the video attachment, unknown to the user, Console Module 200, in conjunction with Enhanced VMM 230 may determine where the attachment is stored and launch the file. In this example, since the attachment is stored in VM 120, the actual processing for the video may be performed within the context of VM 120, thus isolating any potentially harm that the data may cause to the remaining VMs on Host 100. In one embodiment, this scheme may also enhance the user's experience, e.g., VM 120 may be running a real-time operating system and/or other dedicated hardware resources of Host 100, which may enable VM 120 to provide seamless audio/video playback. Certain VMs on Host 100 may always be running (e.g., VMs that containing PVR applications and/or VMs that host personal web servers). An embodiment of the present invention thus does not rely on a user being logged in to Host 100. According to this embodiment Console Module 200 may continue to monitor and manage the data for these VMs even when a user is not (or no longer) logged in.
Unified Desktop Interface 400 illustrated in FIG. 4 is merely an example of an interface that the user may see, in which there is no indication that the host is virtualized. In an alternate embodiment, Unified Desktop Interface 400 may include a view of all the VMs as well as all the applications running in each VM. In yet another embodiment, in a layered VM environment, a unified desktop interface may exist across all VM layers. Alternatively, in a layered VM environment, a unified desktop interface may be provided with each VMM, thus enabling one unified desktop interface to be embedded in the unified desktop environment of a parent VM layer.
Most importantly, by presenting a unified view to the user, embodiments of the present invention significantly improve the usability of multiple VMs simultaneously, because the user's experience may resemble that of a typical desktop PC user, namely one in which the user simply selects an application (i.e., Guest Software) on Host 100 to execute, without needing to be aware of the virtual machines on the PC and/or how to manage or exchange the Guest Software files within these machines. Thus, for example, if the user selects Mail Program 410, as expected, the user may then be presented with the graphical output from Mail Program 410. The user may view this output within Unified Desktop Interface 400 and the underlying interaction with the various VMs on Host 100 may remain invisible to the user, i.e., the user does not know that Mail Program 410 is actually executing in one of the VMs on Host 100.
A third VM patent on security
Intel's Abstract for patent 20060136910: A method, apparatus and system for improving security on a virtual machines host is described. A shared file system on the host may include annotations usable by a service module to access files across VMs and to enforce security policies. The service module may additionally enable a unified user interface to improve usability of the host.
Patent excerpts
Techniques exist to purge viruses from affected computers. Such techniques, however, are often are used only after the virus has been detected and many computers have been infected. New methods are desired that will slow down the propagation of computer viruses and other malicious code, thus allowing the virus detectors to detect and delete the viruses before the damage becomes widespread.
Along with improving the ability to detect and slow such attacks, it is also desirable to prevent or limit damage to users' systems and access to users' data. The ideal world in which users would never run suspicious files will never exist, so a practical solution must recognize this and attempt to prevent or limit these programs from damaging the user's system and accessing the user's data.
Sharing Files: The VM Service Console
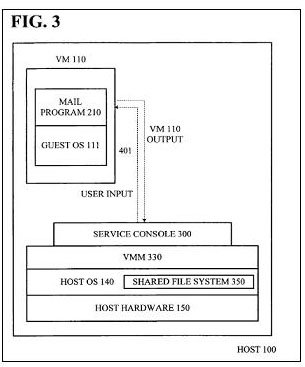
Patent FIG. 3 illustrates conceptually an embodiment of how the service console ("Service Console 300") functions to present Unified Desktop Interface 200 to the user.
In one embodiment, to enable Service Console 300 and/or Unified Desktop Interface 200 (which represents the output in Service Console 300), Host 100 may include a shared file system (illustrated conceptually as "Shared File System 350", contained within Host OS 140). In one embodiment, Shared File System 350 may comprise an extended file system, e.g., existing file systems within Host OS 140 (as illustrated in FIG. 3) may be extended to recognize additional attributes. Regardless of how it is implemented, Shared File System 350 allows files to be shared across VMs, thus enabling Service Console 300 to present the user with Unified Desktop Interface 200 that includes views of the file system.
Operating systems typically include an application (hereafter referred to as a "file manager") that provides users with a graphical or textual view and an interface to the file system. Current virtualization software typically creates a separate file system for each VM on the VM host. As a result, the file manager that runs in each VM is only able to see the file system of that VM. A user may therefore be forced to interact with several file managers to access all of the files the user is working with. According to embodiments of the present invention, by providing a shared file system on Host 100 (e.g., Shared File System 350), the user may interact with a single file manager that interfaces with the Shared File System 350 and yet maintains the security properties of the system.
To enable file sharing, Shared File System 350 may include a scheme for annotating all files on Host 100 with an identifier. The identifier may include various types of information such file ownership, permissions, etc. Thus, for example, when a VM attempts to open a file, the annotation in the file system may be examined to determine whether the VM has the appropriate permissions to access the file. Since the annotation determines the permissions for the file, and Service Console 300 handles the underlying tasks of locating the file, launching the file in the appropriate VM and displaying the output within Unified Desktop Interface 200 (i.e., within the context of Service Console 300), the user need not be aware of any of these actions.
In one embodiment of the present invention, to enhance the security of the VM host, the annotations in Shared File System 350 may be utilized to enforce various policies. In various embodiments, the annotations may define policies for all activities in each VM, including the types of applications that can be installed in various VMs, what files can be used by those applications, what VMs may access each file (regardless of which VM owns the file), etc. The policies may encompass files that exist on Host 100, files that are created on Host 100, as well as files received on Host 100 from remote sources. In one embodiment, the policies specified by the annotations may be enforced by Service Console 300. Thus, for example, the annotations in the file system for certain VMs may include an extremely strict security policy which does not allow the user to import any files into the VM that were not signed by a trusted party.
Additionally, a VM may also have a policy that would not allow a user to export any file to another VM. In other embodiments, various VMs may include a more relaxed policy that allows a user to import data files, but not install new applications. Yet another VM may have an open policy that allows a user to do anything in the VM. Similar to the policy for moving and/or copying files, a policy may also be implemented to monitor movement of information to a "clipboard". It will be readily apparent to those of ordinary skill in the art that the above policies defined by the annotations in the file system and merely exemplary and embodiments of the present invention are not so limited. Instead, embodiments of the present invention may be expanded to include various other types of policies designed to enhance the security of the various partitions on Host 100.
To enhance the security of the system, in one embodiment, VM 120 may only "pull" the "shared" file, to prevent untrusted software from "pushing" its files to trusted VMs. The concept of "pulling" and "pushing" are well known in the art and further description thereof is omitted herein.
Notice
Macsimum News presents only a brief summary of patents with associated graphic(s) for journalistic news purposes as each such patent application and/or grant is revealed by the U.S. Patent & Trade Office. Readers are cautioned that the full text of any patent applications and/or grants should be read in its entirety for further details.
This report is based on Intel's patent application numbers 20060136911 and 20060136910.
neo@macsimumnews.com












