Download an app from the Mac App Store or the Apple App Store, and Apple plans to make sure you’re using it per the company’s enforcement policy, according to a patent (number 20120095877) at the U.S. Patent & Trademark Office.
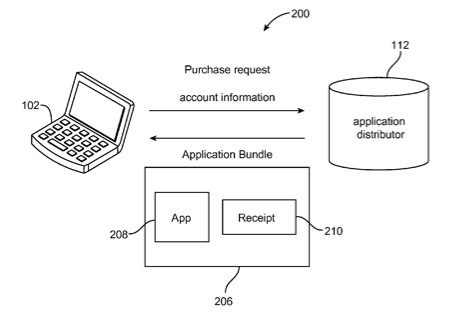
Disclosed are systems, methods, and non-transitory computer-readable media for enforcing application usage policies. As part of an application purchase transaction, the application distributor creates a unique proof of purchase receipt. This receipt can be bundled with the application and delivered to the purchaser. Each machine can maintain an authorization file that lists the users authorized to use applications on that machine.
A system configured to practice the method verifies that a user is authorized to use an application on a machine based on an application proof of purchase receipt and the authorization file. If the application proof of purchase receipt and the authorization file are both valid, the system checks if the user account identifier in the receipt is contained in the authorization file. If so, the user can be considered authorized to use the application on the machine.
Here’s Apple’s summary of the invention: “An important feature of computer software is that a single piece of software can be installed on multiple machines without a need to alter the software. This is advantageous for the software developer because they can develop the software once and then distribute it to many different users without any additional work. It is also advantageous for the user because he or she can move their software from one machine to another, for example, when the user buys a new computer.
“Software portability also makes it possible for a user to buy a single copy of the software and simultaneously install it on multiple computers, which in some situations may be undesirable. For example, some software may be very costly to produce and have a very small target market. In this case, unauthorized copying may prevent the developer from recouping their costs.
“To prevent unauthorized copying, software developers often employ an installation process that requires a unique product key for each installation of the software. This approach prevents unauthorized copying, but it also makes it difficult for a user to migrate from one machine to another. Furthermore, this solution is cumbersome when a software developer has a policy that allows a user to install the software on a specified number of machines.”
The inventors are Jean-Pierre Ciudad, Augustin J. Farrugia, David M’Raihi, Bertrand Mollinier Toublet, Gianpaolo Fasoli andd Nichoals T. Sullivan.