A new patent (number 20100138654) has appeared at the US Patent & Trademark Office for a system of digital rights management (DRM) that would identify the authenticity of a device based on the unique physical emission properties of a “particle gun.” The invention invention relates to DRM and more specifically to authentication or hashing functions.
Here’s Apple’s background and summary of the invention: “The field of DRM involves code protection, code obfuscation and various other software security mechanisms. Cryptography is one such way to protect information. Cryptography is the practice of hiding information; encryption is the process of converting intelligible information (plaintext) into unintelligible information (ciphertext); and decryption is the process of converting ciphertext back into plaintext. Authentication is a software security mechanism that establishes or confirms an entity as authentic, or true.
“Hashing is also often utilized in authentication. Hashing is the process of producing a value (typically fixed length called a hash or digest) based on the input and has three main properties: it is easy to calculate a hash or digest for any given data, it is extremely difficult to calculate an input with a given hash or digest, and it is extremely unlikely that two different messages will have the same hash or digest.
“In all of these areas, namely encryption, decryption, authentication, hashing, etc., that are included in cryptography, there is a set of basic tools or functions that are widely used, for instance hash functions and derivation functions. Authentication systems often utilize functions to derive information. The process of derivating information from provided data is iterated numerous times to ensure that the final information cannot be used to get details about the initial information. Allowing initial information to be recovered from final information is a major flaw in cryptography systems since the objective of cryptographic systems is to protect the initial information.
“Many authentication systems exist. Accordingly, what is needed in the art is an improved way to perform authentication, such that it is difficult to extract initial information from final information.
“Additional features and advantages of the invention will be set forth in the description which follows, and in part will be obvious from the description, or may be learned by practice of the invention. The features and advantages of the invention may be realized and obtained by means of the instruments and combinations particularly pointed out in the appended claims. These and other features of the present invention will become more fully apparent from the following description and appended claims, or may be learned by the practice of the invention as set forth herein.
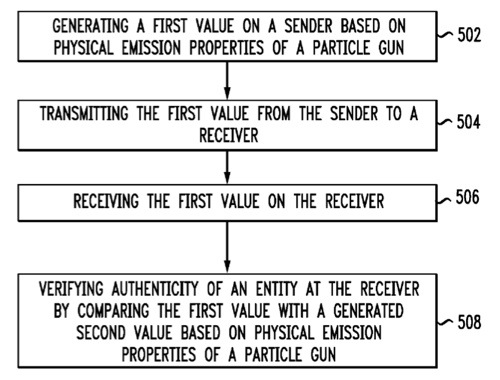
“Disclosed are systems, methods, and tangible computer readable-media for authentication based on physical particle gun emissions. The method includes generating a first value on a sender based on physical emission properties of a particle gun; transmitting the first value from the sender to a receiver; receiving the first value on the receiver; and verifying the authenticity of an entity at the receiver by comparing the first value with a second value generated at the receiver. Generating the first and second values is based at least in part on input data that provides physical emission properties of the particle gun including at least one of initial speed, electromagnetic fields, mass, electronic charge and time. The method of authenticating based on physical particle gun emissions makes it difficult to recover initial input from output values.
“In another aspect, the method of authentication includes generating a challenge on a sender based on physical emission properties of a particle gun and a secret value, transmitting the challenge from the sender to a receiver, receiving the challenge on the receiver and verifying authenticity of an entity at the receiver by comparing the challenge with a value generated at the receiver.
“In yet another aspect, the method of authentication includes generating a first challenge value on a sender, transmitting the first challenge value from the sender to a receiver, receiving the first challenge value on the receiver, generating a second challenge value at the receiver and computing a receiver response based on the first challenge value, the second challenge value and a secret. The computation of the receiver response can be based on physical emission properties of a particle gun. The method further includes transmitting the receiver response to the sender and verifying authenticity of an entity at the sender by comparing an expected value of the receiver response with a calculated value based on the first challenge value, the second challenge value, a secret and being based on the physical emission properties of the particle gun.”
The inventors are Betouin Pierre, Ciet Mathieu and J. Farrugia.
Three other continuation patents from Apple have also appeared at the US Patent & Trademark Office.
Patent number 20100138739 involves text flow in and around irregular containers. Providing text flow in or around an irregular container, such as a non-rectangular graphic, is disclosed. In the case of flow around a container, the intersection, if any, between a proposed text rectangle and the irregular container is determined. A valid rectangle, if any, that is not within the bounds in the x-direction of an area of intersection between the proposed text rectangle and the graphic is identified as a valid text area within the proposed text rectangle. In the case of flow around a container, one or more difference areas, if any, in which a proposed text rectangle is present but the container is not present are found. A valid rectangle, if any, that is not within the bounds in the x-direction of any of said one or more difference areas is identified as a valid text area within the proposed text rectangle. The inventors are Steve Sprang and Scott Lindsey.
Patent number 20100134507 is for a method and apparatus for frame buffer management. At least one embodiment of the present invention dynamically enables or disables the use of a virtual frame buffer, which is not under control of graphics hardware of a data processing system, without restarting the graphical user interface system (e.g., the window system) of the data processing system. For example, in response to the addition or removing of a frame buffer that is under control of a graphics controller (e.g., due to the activation or deactivation of the graphics controller, or the hot plug-in or hot disconnection of the graphics controller), the virtual frame buffer is disabled or enabled respectively. The inventors are Michael James Paquette and Simon Douglas.
Patent number 20100138056 is for an apparatus for air cooling of an electronic device. A contoured panel channels a flow of air within the housing of an electronic device so as to channel the flow of air more directly over heat producing elements such as the microprocessor and peripheral cards. A sensor can also be employed to determine whether the panel is present and properly placed. If not, measures can be taken to reduce the heat generated by the heat producing elements. For example, a warning can be displayed, or the microprocessor can be instructed to enter sleep mode. The inventors are Steven Holmes and Douglas L. Heirich.